It’s Time to Migrate to Windows Logon with Push Notification

In light of constantly evolving cybersecurity risks, businesses must take strong measures to secure internal and remote network access by employees.
Today’s workforce requires convenient anytime, anywhere access to web, mobile and cloud networks, applications and resources. Clearly, timely access to information drives business forward.
At the same time, organizations must prevent security breaches, and maintain continuous compliance with security and privacy laws, regulations and standards, such as the GDPR and PCI DSS 3.2. To achieve both strong security and optimal employee experience, security teams need to consider adopting, or migrating to, Windows logon with push notification.
Using two-factor authentication for employees’ Windows logon (and the related network login) is a vast improvement over static passwords. According to Verizon’s latest Data Breach Investigations report, 81 percent of hacking-related data breaches involve weak or stolen passwords. Verizon recommends two-factor authentication as one of the cornerstones to protect against cyberattacks and limit the damage resulting from lost or stolen credentials.
Legislation and Industry Standards
The increase in cyberattacks on businesses has triggered new legislation and industry standards. The Global Data Protection Regulation (GDPR) and Payment Card Industry Data Security Standards (PCI DSS) 3.2 are two examples, both of which define measures to mitigate risk.
For example, Article 32 of the GDPR mandates that companies secure personal data by implementing “appropriate technical and organizational measures to ensure a level of security appropriate to the risk.”
While this may seem ambiguous, the European Union Agency for Network and Information Security (ENISA) has the role of advising how to implement and comply with the GDPR, which goes into effect May 25, 2018.
In the Guidelines for SMEs on the security of personal data processing, ENISA addresses compliance with the GDPR’s access control and authentication requirements. The agency recommends implementing two-factor authentication in high-risk cases and in certain medium impact cases:
“Two-factor authentication should preferably be used for accessing systems that process personal data. The authentication factors could be passwords, security tokens, USB sticks with a secret token, biometrics, etc.”
ENISA also mentions that use of mobile devices increases exposure to theft and accidental loss of the device. Since mobile devices are likely to be used for personal purposes as well, special care must be taken to not compromise business-related data. As a result, the ENISA guidelines advise that:
“Two-factor authentication should be considered for accessing mobile devices, and personal data stored at the mobile device should be encrypted.”
PCI DSS 3.2
On February 1, 2018, Requirement 8.3 of the PCI-DSS 3.2 went into effect, making multi-factor authentication mandatory for non-console access to computers and systems handling cardholder data, and remote access to the cardholder data environment (CDE).
- Requirement 8.3.1 addresses multi-factor authentication for all personnel with non-console administrative access to the cardholder data environment (CDE). Non-console access means that it is performed over a network rather than via a direct physical connection. It can happen from within internal, as well as external or remote, networks.
- Requirement 8.3.2 incorporates the former Requirement 8.3, and addresses multi-factor authentication for remote access to the CDE. This requirement is intended to apply to all personnel – including general users, administrators and vendors (for support and maintenance).
Windows Logon with Two-factor Authentication
Using two-factor authentication for your employees’ Windows logon (and the related network login) secures access to all critical applications and sensitive data stored on an employee’s laptop and the corporate network. The combination of Windows logon and two-factor authentication also secures any remote access over a Virtual Private Network or Virtual Desktop Infrastructure.
Two-factor authentication for Windows logon allows employees to log on to their Windows desktop on the network with a one-time password (OTP). The two required authentication factors consist of:
- A one-time password (something the user has, e.g. a hardware token or a smartphone with an OTP app, provisioned with a secure key to generate the OTP)
- A static password (something the user knows)
Both authentication factors are independent and the one-time password is not reusable. This complies with the requirements for two-factor authentication.
Two-factor authentication for Windows logon is installed as a small software module on the employee’s Windows environment. It can be installed on desktop PCs, laptops and servers. As soon as this is set up, it replaces the original logon window with a version that will verify the OTP generated by a software or hardware client.
Push Notification
Instead of entering the OTP in the Windows password field, employees have another option.
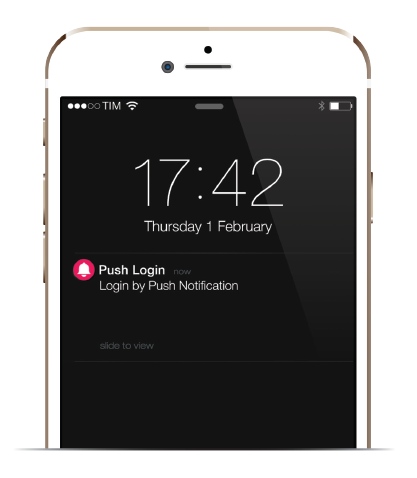
They can use an OTP app on their smartphone to facilitate the logon process. During the authentication process when logging on to Windows, the employee receives a notification prompt on their mobile device, and authenticates with a simple tap on the device.
This push notification is an out-of-band (OOB) authentication method that uses a push mode to enable the OTP app on the employee’s mobile device to authenticate them automatically.
Push notification will have a strong impact on the authentication market because it combines higher security with an improved user experience, at a lower total cost of ownership. This represents the holy grail for authentication, with analysts now recommending that organizations adopt or migrate to mobile push notification.
Key reasons to consider implementing push notification:
- Stronger security. There is no need to type in the OTP, which means the password can’t be intercepted by keyloggers, for instance. In addition, the OTP app can be secured with a PIN or biometrics, as well as Mobile Device Management or application shielding.
- Improved user experience. In addition to saving the step of typing in the OTP, the employee is proactively informed about the context since login or transaction details are displayed right in the notification. A single click to confirm the employee received the push notification might be sufficient to authenticate. When higher security is required, the organization can layer in local authentication factors like phone PIN, or biometric authentication, such as fingerprint or face recognition.