Document Verification: 4 Levels of Security to Verify IDs Online

As more financial services become digitized, it is essential for financial institutions to offer customers fast, reliable, mobile, and online access to products and services. This often means rethinking the customer journey, particularly the stage in which a customer and financial institution first establish a relationship – onboarding and account origination.
Account opening requires mutual trust between a customer and a financial institution (FI). Customers need to trust the FI to keep their personal details secure and private, and in return, the FI needs to verify that the customer is who they say they are. Establishing digital trust requires digital identity verification capabilities.
In this article we offer an in-depth guide to one of the strongest digital identity verification solutions for establishing digital trust – Automated ID Document Verification powered by artificial intelligence (AI).
Common Digital Identity Verification Solutions
The most commonly used digital identity verification methods include:
- Facial Biometric Verification – Comparing a selfie with an image on a validated ID document (e.g., image on a driver’s license).
- ID Document Verification – Uses AI and advanced algorithms to verify that an ID document is legitimate, using an image of that document taken by the customer on their mobile phone.
- One-Time Passcode (OTP) Verification – A one-time passcode is transmitted to the applicant during the account opening/application process.
- Knowledge-Based Authentication (KBA) – The customer is asked to answer a number of questions based on their personal information, e.g., based on information from credit bureaus.
To deliver a fast, online customer experience while also establishing trust, the best combination of these digital identity verification methods is ID document verification and facial recognition. These technologies make it possible to digitally verify the identity of almost all prospective customers using a government-issued ID document such as a driver’s license, passport, or National ID.
How It Works: Automated ID Document Verification with Artificial Intelligence
Imagine a scenario in which a customer is applying to open a new current/checking account using a bank’s mobile app. The bank has automated ID document verification integrated into their mobile account opening process to establish a trusted identity for the applicant.
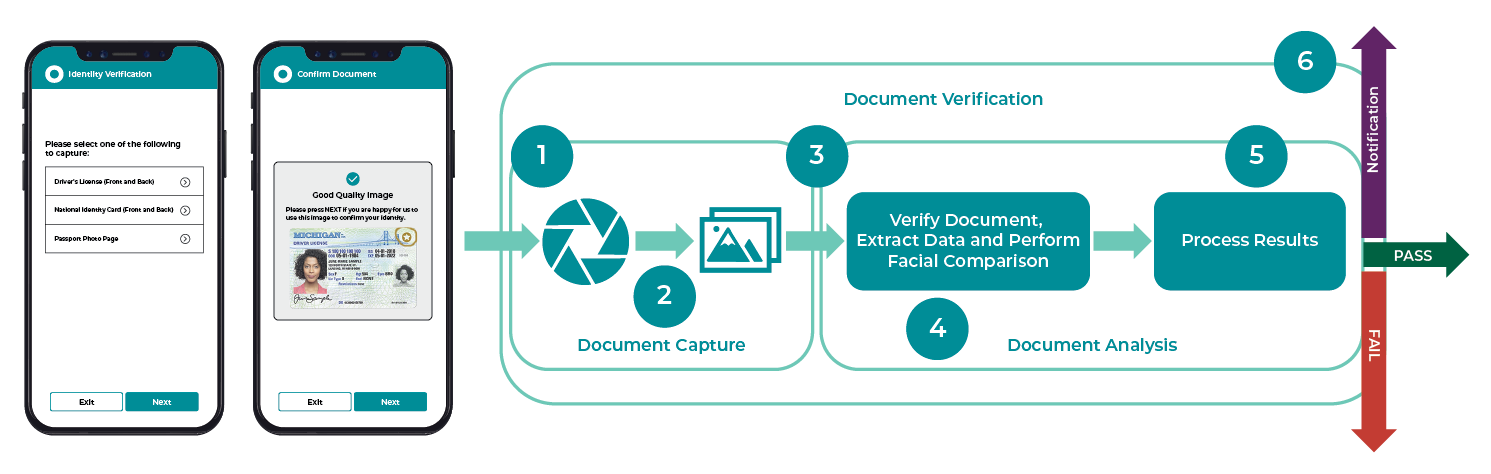
There are two main components of the feature: document capture and document analysis.
Document Capture Stage:
- The customer starts the account opening process and is asked to capture images of their Identity Document using the camera on their mobile phone (two images for driver’s licenses and National Identity Documents and one image for passports).
- The document verification technology performs image quality checks on the captured image(s) to ensure they are of sufficient quality that they can be verified.
Document Analysis Stage:
- The captured image(s) of the ID document are sent for verification.
- The image(s) are analyzed using artificial intelligence, data points are extracted (e.g., name, expiry date) and the Identity Document is verified.
- The account opening solution receives the response/result, performs a number of data matches, and decides whether or not to allow the applicant to continue.
- The account opening solution sends a notification to the applicant to inform them of the decision.
The time this process takes depends on the level of document analysis configured as part of the process. Determining the level of analysis involves a balancing of customer experience considerations and risk.
There are four levels of document analysis security, each of increasing security.
Four Levels of Document Analysis Security for ID Document Verification
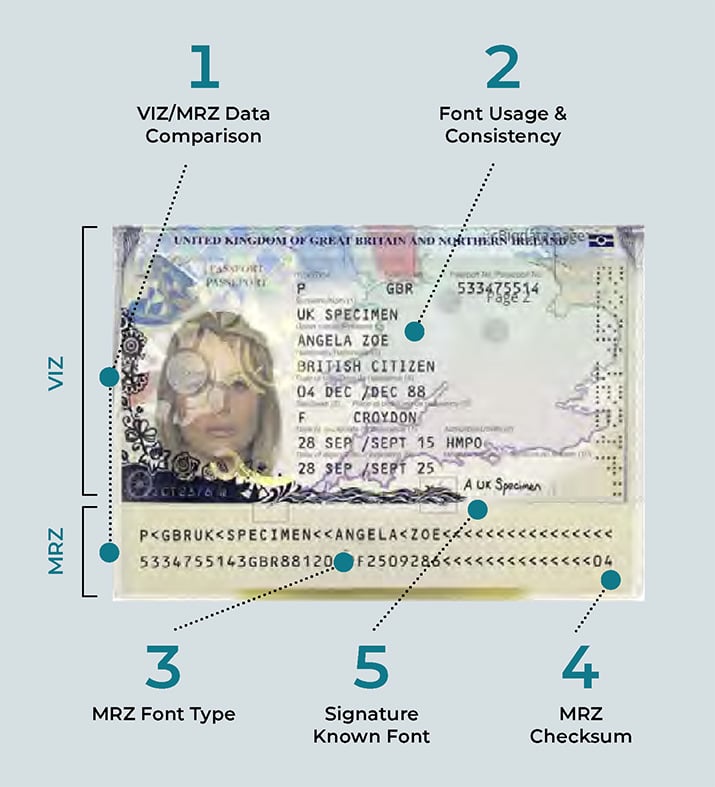
1. Level 1: Text Analysis - Examines the Visual Inspection Zone (VIZ) and Machine-Readable Zone (MRZ) for font, correct usage of font, logic, and positioning.
Description of Analysis:
- VIZ/MRZ Data Comparison: Comparing that that they relate to each other (MRZ cannot replicate accents and special characters)
- Font Usage & Consistency: Are the fonts detected as expected?
- MRZ Font Type: Is it the correct font?
- MRZ Checksum: Is this the expected value?
- Signature Known Font: Is a font being used instead of an actual signature?
Customer Experience:
- Very good - Little friction for the customer.
2. Level 2: Analysis of Replicable Patterns and Features - Analyzes pattern recognition, metatext and chip detection.
Description of Analysis:
- Human Face detection: Is it an actual face as opposed to an illustration?
- Portrait Color, Positioning & Integration: Is it all as expected?
- Visible Security Features: NFC (Near Field Communications) chip position and appearance, and printing technique.
Customer Experience:
- Good - High resolution images required.

3. Level 3: Analysis of Difficult to Replicate Patterns and Features - Analyzes micro-printing, kinegram, OVI, and special inks.
Description of Analysis:
- Analysis of micro-printing.
- Analysis of Kinegram security holograms.
- Analysis of OVI (Optically Variable Ink)®: OVI has a two-color shift, immediately apparent when viewed at different angles. As a high security product, OVI is instantly recognized and its colour shift cannot be photocopied or reproduced.
- UV: Appearance in UV light.
- Analysis of Optically Variable Device (OVD): OVD is an iridescent or non-iridescent security feature that exhibits different information, such as movement or color changes, depending on the viewing and/or lighting conditions. OVDs cannot be photocopied or scanned, nor can they be accurately replicated or reproduced.
Customer Experience:
- Medium friction - Special printers and material is required. Control of flash generally required, in some cases specialist hardware may be required.

4. Level 4: NFC Chip Reading - Extraction of full image and data, and secured with a digital certificate.
Description of Analysis:
- Provides a very high security level as the chip contains the picture (better quality so better face com-parison experience) and the person’s personal data, so any physical manipulation of the document can be detected.
- Unequivocal confirmation of the authenticity of chipped identity documents.
- No manual input or OCR (Optical Character Recognition) mistakes.
- Digital signature is used in the chip.
Customer Experience:
- High friction - Access to chip reader is required, which requires a native app or specialist hardware. NFC is a better user experience if the user already has the app; less so if forced to download an app.

How to Select the Best Document Analysis Level for a Use Case
When it comes to the analysis of ID documents, there often is a trade-off between ease of use and security. For most online account openings, the customer journey should be secure but still easy for the applicant. Adding friction to the customer journey can lead to applicant abandonment. Recent reports have suggested that abandonment due to friction during account opening can be as high as 55% for some products. Financial institutions must therefore balance the user experience with the risk associated to the product to find the tradeoff between a good user experience and risk management.
ISO 29115 Level of Assurance standards can also help financial institutions define the desired level of assurance for each customer journey. Standards can vary from one region to another. In the US, the financial services industry relies on NIST standards. In the EU, standards are defined by the eIDAS regulation. When evaluating the types of identity verification methods to deploy for your specific use case, be sure to evaluate the level of risk you’re willing to assume within your institution. A good way to achieve this is to perform a risk assessment of the transactions or services that require identity verification. Once this is completed, you can select the appropriate level of assurance and identity verification methods that strike the right balance between security and customer experience.
Conclusion
Automated ID document verification offers financial institutions a way to more effectively verify the identity of new and existing customers. When integrated into a digital account opening process, this method of digital identity verification allows any person to open a bank account remotely. Financial institutions looking to implement automated ID document verification into their account opening process should determine the level of document analysis in order to balance ease of use with security requirements.
Automated ID document verification can also be combined with facial comparison as part of digital identity verification during mobile account opening. Facial recognition, which is 99.7% accurate and getting more so by the year, according to NIST, is a particularly useful biometric modality for digital account opening as it helps fight sophisticated application fraud attacks and the user experience of capturing a “selfie” is very intuitive and convenient.










